Home » Posts tagged 'networking'
Tag Archives: networking
Azure Virtual Network peering
Virtual network peering is used to connect two vnets to each other
There are two types of Azure virtual network peering
Regional and Global
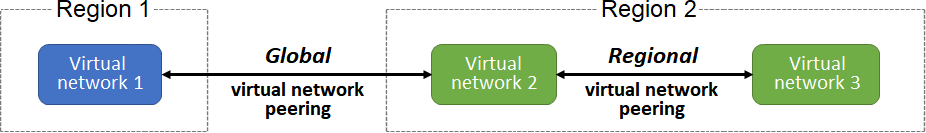
Regional virtual network peering connects two vnets from the same region
Regional peering can be created between vnets that are in the same public region
Global virtual network peering connects two vnets located in different regions
Global peering can be done between vnets located in any region
Traffic between peering vnets is private and transits over Azure’s private backbone
Peering can be used to transfer resources between Azure subscriptions, and between Azure regions
Consider a scenario in which three virtual networks in the same region are connected via virtual network peering. Virtual network A and virtual network B each have peering with a hub virtual network. The hub virtual network contains several resources, including a gateway subnet and an Azure VPN gateway. The VPN gateway is configured to allow VPN gateway transit. Virtual network B accesses resources in the hub, including the gateway subnet, using a remote VPN gateway.
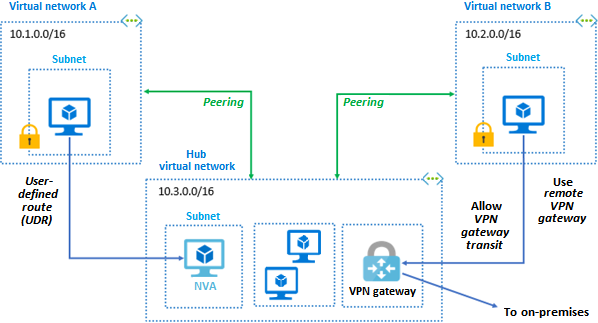
A virtual network can have only one VPN gateway
Gateway transit is supported in both regional and global peering
When VPN Gateway transit is allowed, the virtual network can communicate with resources outside the peering. In our example illustration, the subnet gateway within the hub virtual network can complete tasks such as:
Use a site-to-site VPN to connect to a local network.
Using a vnet connection – vnet
Azure vNet Reserved IP
For each subnet, Azure reserves five IP addresses.
The first four addresses and the last address are reserved.
Let’s examine the reserved addresses in an IP address range of 192.168.1.0/24.
192.168.1.0 This value identifies the virtual network address.
192.168.1.1 Azure configures this address as the default gateway.
192.168.1.2 and 192.168.1.3 Azure maps these IP addresses to Azure’s DNS service
192.168.1.255 This value provides the broadcast address of the virtual network.
Routing between subnets
By default, Azure routes network traffic between all subnets in a virtual network. You can override Azure’s default routing to prevent Azure from routing between subnets. You can also override the default to route traffic between subnets via a virtual network appliance. If you need traffic between resources in the same virtual network to go through a network virtual appliance, you need to distribute the resources to different subnets.